Comprehensive account enrichment
Computational research that surfaces the facts in minutes. And sometimes, seconds.
Collate powerfully and instantly
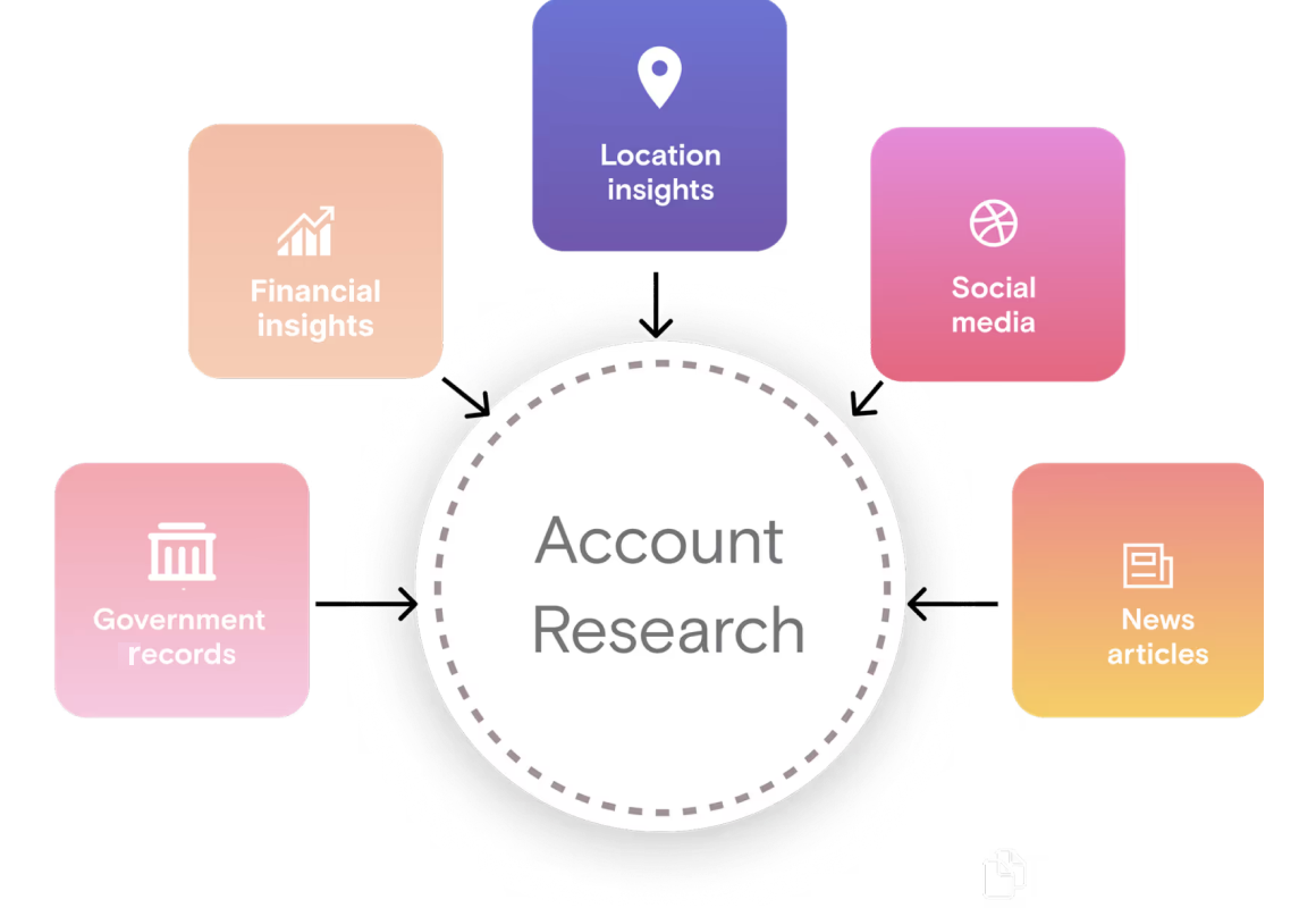
Outside-in account enrichment
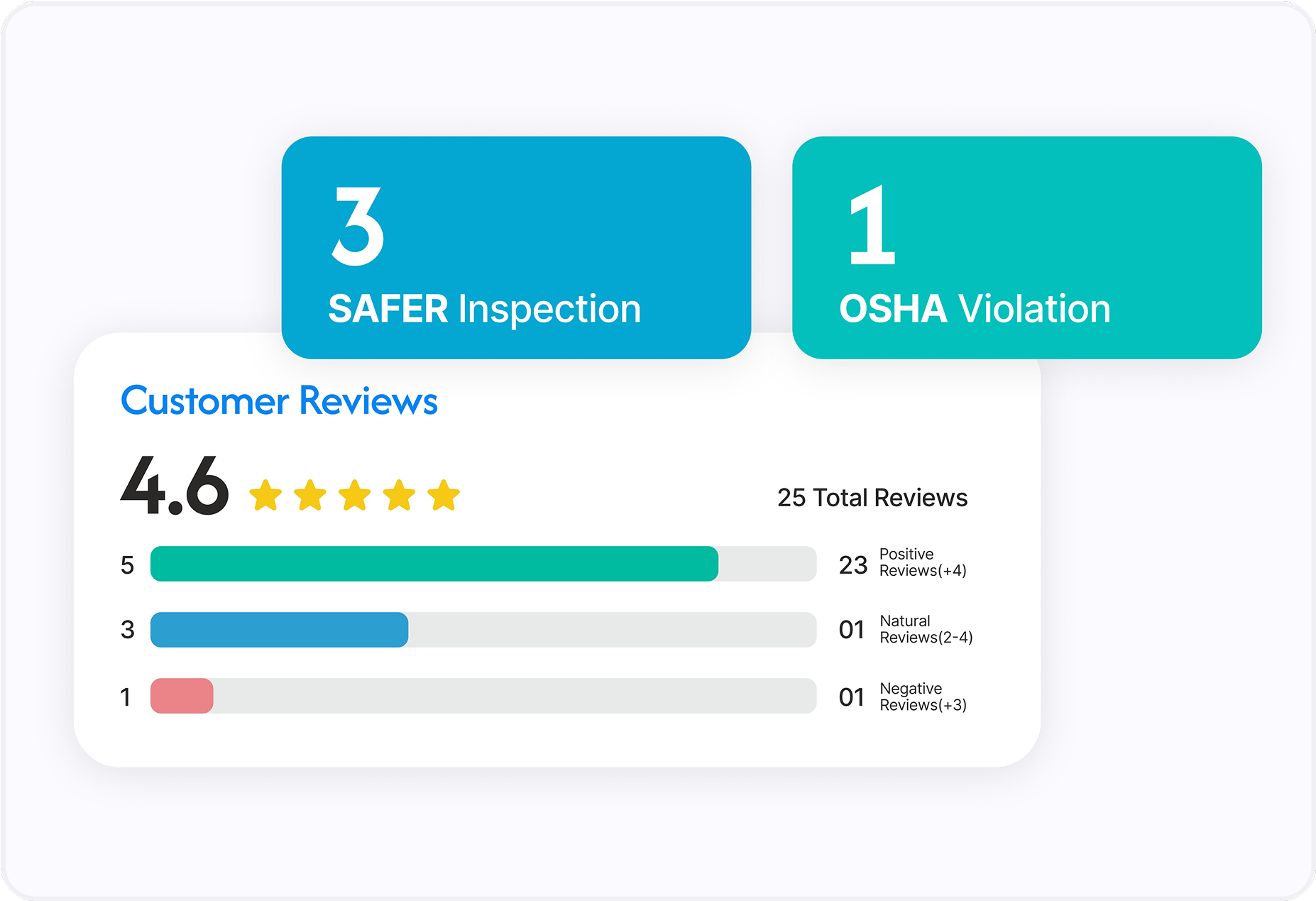
Pull authoritative records from government and regulatory sources.
Aggregate public signals from news and social channels.
Map NAICS and SIC codes to classify industry exposure precisely.
Highlight mismatches across sources so you can trust the file at a glance.
Plug into any source
Ingest web and internal feeds instantly
Integrate new web sources and internal feeds in minutes.
Pull data via email, UI, API, SharePoint, SFTP, or drives.
Normalize and merge disparate feeds into one enriched profile.
Highlight patterns that drive smarter decisions.
Deliver results directly to your inbox, API, or system record.
Trustworthy indicators only
Validate every signal for true confidence
Validate source credibility and provenance before surfacing findings.
Verify conflicting claims across documents and web sources.
Summarize articles and posts into concise, review-ready briefs.
Flag outdated or contradictory information for quick reconciliation.


Decisions with real impact
Surface forward-looking insights for underwriters
Reveal external trends and events that affect appetite.
Score accounts for appetite fit so you know what to pursue first.
Prioritize submissions based on combined external and internal signals.
Recommend next steps to accelerate quote and bind decisions.
Win with real advantage
Fast, plug and play research that scales
Return enriched account profiles within minutes, not days.
Start with zero code integration from day one.
Increase underwriter throughput and decision quality across the book.


85%
Faster Underwriting

32%
More GWP

700bps
Loss Ratio Improvement
Ironclad Data Security
Our commitment to data integrity is paramount, and we take pride in meticulously protecting your invaluable information. All customer data is housed in the US AWS regions on SOC 2 and ISO 27001 certified infrastructure to deliver the operational rigor enterprise teams expect. We encrypt data at rest with AES 256 and in transit with TLS 1.2, enforce least privilege through role based access controls, and defend applications with a web application firewall and AWS Shield. Comprehensive logs are retained for 90 days to enable rapid investigation and compliance, so you can move fast with absolute confidence.


Backed by

Member Of





